Explain Internet Security Framework
Software to train employees on security topics including phishing, email security, safe web browsing, and more.
Key Features and Benefits:
Deploy mock cyber-attacks to help employees become receptive to more in-depth training
Create training assignments for everyone at once, or for groups of employees you define
Select from a comprehensive set of software-based security training courses - under 15 minutes each
Monitor employee completion of assignments and deliver automatic reminders
Identify the users who have the best or worst understanding of critical risk areas
Show measurable knowledge improvement over time with easy-to-read reports
Train global employees in multiple languages, including: Spanish, Chinese, Portuguese, French, Japanese, Korean, and many more
Manage all your security training programs from one cloud-based system that is continually updated with new content about the latest cyber threats
Get started here.

Expert Joe Granneman introduces several IT security frameworks and standards, and offers advice on choosing the right one for your organization.
Plan, deploy, secure, and manage Microsoft software on your IT systems with Solution Accelerators.
Security Awareness Training: The Complete Solution

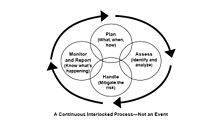
Plan-Do-Check-Act Cycle
ENISA: Risk Management and Isms activities
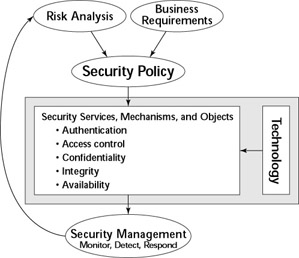
An information security management system 1 ISMS is a set of policies concerned with information security management or IT related risks. The idioms arose primarily out of BS 7799.
The governing principle behind an ISMS is that an organization should design, implement and maintain a coherent set of policies, processes and systems to manage risks to its information assets, thus ensuring acceptable levels of information security risk.
Contents
1 ISMS description
2 Need for an ISMS
3 Critical success factors for ISMS
4 Dynamic issues in ISMS
5 See also
6 Notes and references
ISMS description edit
As with all management processes, an ISMS must remain effective and efficient in the long term, adapting to changes in the internal organization and external environment. ISO/IEC 27005 therefore incorporated the Plan-Do-Check-Act PDCA, or Deming cycle, approach:
The Plan phase is about designing the ISMS, assessing information security risks and selecting appropriate controls.
The Do phase involves implementing and operating the controls.
The Check phase objective is to review and evaluate the performance efficiency and effectiveness of the ISMS.
In the Act phase, changes are made where necessary to bring the ISMS back to peak performance.
ISO/IEC 27005 is a risk based information security standard, which means that organizations need to have a risk management process in place. The risk management process fits into the PDCA model given above. 2
However, the latest standard, ISO/IEC 27013, does not emphasise the Deming cycle anymore. The ISMS user is free to use any management process improvement approach like PDCA or Six Sigmas DMAIC.
Another competing ISMS is Information Security Forum s Standard of Good Practice SOGP. It is more best practice-based as it comes from ISF s industry experiences.
Some best-known ISMSs for computer security certification are the Common Criteria CC international standard and its predecessors Information Technology Security Evaluation Criteria ITSEC and Trusted Computer System Evaluation Criteria TCSEC. 3
Some nations publish and use their own ISMS standards, e.g. the Department of Defense DoD Information Technology Security Certification and Accreditation Process DITSCAP of USA, the Department of Defense Information Assurance Certification and Accreditation Process DIACAP of USA, the German IT baseline protection, ISMS of Japan, ISMS of Korea, Information Security Check Service ISCS of Korea. 3
Other frameworks such as COBIT and ITIL touch on security issues, but are mainly geared toward creating a governance framework for information and IT more generally. COBIT has a companion framework Risk IT dedicated to Information security.
The below table provides a certification structure comparison of some of the best-known ISMSs: 3
BS 7799
Common Criteria
IT Security Evaluation Criteria
Operation Area
England
About 25 Countries
European Countries
Basic Structure
- 6 Management phases
- 11 Security domains
- 139 Control objectives
- 133 Security controls
- 3 Parts
- 11 Security functional requirements
- 8 Assurance requirements
- 4 Phases
- 6 Levels
Management Process
1- Define policy
2- Define scope
3- Assess risk
4- Manage risk
5- Select controls to be implemented and applied
6- Prepare a statement of applicability
1- PP/ST introduction
2- Conformance claims
3- Security problem definition
4- Security objectives
5- Extended components definition
6- Security requirements
7- TOE summary specification
1. Requirements
2- Architectural Design
3- Detailed Design
4- Implementation
Difference of Process
Emphasis on managerial security
Emphasis on technical security
Specification Control Point
Provide best code of practice for information security management
Provide common set of requirements for the security functionality of IT products
Evaluation Method
Use the PDCA model cycle
Follow each certification evaluation procedure
Follow commission of European communities
There are a number of initiatives focused to the governance and organizational issues of securing information systems having in mind that it is business and organizational problem, not only a technical problem:
Federal Information Security Management Act of 2002 is a United States federal law enacted in 2002 that recognized the importance of information security to the economic and national security interests of the United States. 4 The act requires each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. 4 5
Governing for Enterprise Security Implementation Guide 6 of the Carnegie Mellon University Software Engineering Institute CERT is designed to help business leaders implement an effective program to govern information technology IT and information security.
A Capability Maturity Model CMM for system security engineering was standardized in ISO/IEC 21827.
Information Security Management Maturity Model known as ISM-cubed or ISM3 is another form of ISMS. ISM3 builds on standards such as ISO 20000, ISO 9001, CMM, ISO/IEC 27001, and general information governance and security concepts. ISM3 can be used as a template for an ISO 9001-compliant ISMS. While ISO/IEC 27001 is controls based, ISM3 is process based and includes process metrics. ISM3 is a standard for security management how to achieve the organizations mission despite of errors, attacks and accidents with a given budget. The difference between ISM3 and ISO/IEC 21827 is that ISM3 is focused on management, ISO 21287 on Engineering.
Need for an ISMS edit
Security experts say: 7
information technology security administrators should expect to devote approximately one-third of their time addressing technical aspects. The remaining two-thirds should be spent developing policies and procedures, performing security reviews and analyzing risk, addressing contingency planning and promoting security awareness;
security depends on people more than on technology;
employees are a far greater threat to information security than outsiders;
security is like a chain. It is only as strong as its weakest link;
the degree of security depends on three factors: the risk you are willing to take, the functionality of the system and the costs you are prepared to pay;
security is not a status or a snapshot, but a running process.
These facts inevitably lead to the conclusion that security administration is a management issue, and not a purely technical issue. 7
The establishment, maintenance and continuous update of an ISMS provide a strong indication that a company is using a systematic approach for the identification, assessment and management of information security risks. Critical factors of ISMS:
Confidentiality: Protecting information from unauthorized parties.
Integrity: Protecting information from modification by unauthorized users.
Availability: Making the information available to authorized users.
A company will be capable of successfully addressing information confidentiality, integrity and availability CIA requirements which in turn have implications:
business continuity;
minimization of damages and losses;
competitive edge;
profitability and cash-flow;
respected organization image;
legal compliance
The chief objective of information security management is to implement the appropriate measurements in order to eliminate or minimize the impact that various security related threats and vulnerabilities might have on an organization. In doing so, information security management will enable implementing the desirable qualitative characteristics of the services offered by the organization i.e. availability of services, preservation of data confidentiality and integrity etc.. 7 By preventing and minimizing the impacts of security incidents, ISMS ensures business continuity, customer confidence, protect business investments and opportunities, or reduce damage to the business. 8
Large organizations, banks and financial institutes, telecommunication operators, hospital and health institutes and public or governmental bodies have many reasons for addressing information security very seriously. Legal and regulatory requirements which aim at protecting sensitive or personal data as well as general public security requirements impel them to devote the utmost attention and priority to information security risks. 7
Under these circumstances, the development and implementation of a separate and independent management process - namely an ISMS - is the only alternative. 7
The development of an ISMS framework based on ISO/IEC 27005 entails the following six steps: 7
Definition of security policy,
Definition of ISMS scope,
Risk assessment as part of risk management,
Risk management,
Selection of appropriate controls
Statement of applicability
Critical success factors for ISMS edit
To be effective, the ISMS must: 7
have the continuous, unshakeable and visible support and commitment of the organization s top management;
be managed centrally, based on a common strategy and policy across the entire organization;
be an integral part of the overall management of the organization related to and reflecting the organization s approach to risk management, the control objectives and controls and the degree of assurance required;
have security objectives and activities be based on business objectives and requirements and led by business management;
undertake only necessary tasks and avoiding over-control and waste of valuable resources;
fully comply with the organization philosophy and mindset by providing a system that instead of preventing people from doing what they are employed to do, it will enable them to do it in control and demonstrate their fulfilled accountabilities;
be based on continuous training and awareness of staff and avoid the use of disciplinary measures and police or military practices;
be a never ending process;
Dynamic issues in ISMS edit
There are three main problems which lead to uncertainty in information security management systems ISMS : 9
Dynamically changing security requirements of an organization
Rapid technological development raises new security concerns for organizations. The existing security measures and requirements become obsolete as new vulnerabilities arise with the development in technology. To overcome this issue, the ISMS should organize and manage dynamically changing requirements and keep the system up-to-date. 9
Externalities caused by a security system
Externality is an economic concept for the effects borne by the party that is not directly involved in a transaction. Externalities could be positive or negative. The ISMS deployed in an organization may also cause externalities for other interacting systems. Externalities caused by the ISMS are uncertain and cannot be predetermined before the ISMS is deployed. The internalization of externalities caused by the ISMS is needed in order to benefit internalizing organizations and interacting partners by protecting them from vulnerable ISMS behaviors. 9
Obsolete evaluation of security concerns
The evaluations of security concerns used in ISMS become obsolete as the technology progresses and new threats and vulnerabilities arise. The need for continuous security evaluation of organizational products, services, methods and technology is essential to maintain an effective ISMS. The evaluated security concerns need to be re-evaluated. A continuous security evaluation mechanism of ISMS within the organization is a critical need to achieve information security objectives. The re-evaluation process is tied with dynamic security requirement management process discussed above. 9
See also edit
Computer security portal
Asset computing
Attack computing
CERT
COBIT
ENISA
Enterprise architecture
FISMA
Information security management
IT governance
IT risk
ISO 9001
ISO/IEC 27001
ISO/IEC 27002
ISO/IEC 27004
ISO/IEC 27005
NIST
Security control
Security information and event management
Threat computer
Vulnerability computing
WARP information security
Notes and references edit
Security management system s usability key to easy adoption. sourcesecurity.com. Retrieved 22 August 2013.
Humphreys, Edward 8 March 2011. Information security management system standards. Datenschutz und Datensicherheit - DuD 35 1 : 7–11. doi:10.1007/s11623-011-0004-3.
a b c Jo, Heasuk; Kim, Seungjoo; Won, Dongho 1 January 2011. Advanced information security management evaluation system. KSII Transactions on Internet and Information Systems 5 6 : 1192–1213. doi:10.3837/tiis.2011.06.006.
a b NIST: FISMA Overview
Caballero, Albert. 2009. 14. Computer and Information Security Handbook. Morgan Kaufmann Publications. Elsevier Inc. p. 232. ISBN 978-0-12-374354-1.
CERT Governing for Enterprise Security Implementation Guide
a b c d e f g Enisa Risk management, Risk assessment inventory, page 8
Ma, Qingxiong; Schmidt, Mark B.; Pearson, Michael 2009. An integrated framework for information security management. Review of Business 30 1 : 58–69. Retrieved 26 October 2013.
a b c d Abbas, Haider; Magnusson, Christer; Yngstrom, Louise; Hemani, Ahmed 1 January 2011. Addressing dynamic issues in information security management. Information Management Computer Security 19 1 : 5–24. doi:10.1108/09685221111115836. access-date requires url help
Retrieved from https://en.wikipedia.org/w/index.php.title Information_security_management_system oldid 697390393
Categories: Data security.
Jun 03, 1996 Microsoft Announces Internet Security Framework. The Internet Security Framework includes support for single logon for the Internet and also.
Smart Protection Network provides global threat intelligence that enables cloud data mining framework technologies to reduce and block the latest web threats in real-time.
Understanding Internet Security What you need to protect yourself online. 1 SECTION ONE Internet Security: What it is, and why you need it.
Techopedia explains Internet Security Internet security relies on specific resources and standards for protecting data that gets sent through the Internet.
- This chapter provides an overview of. NET Framework security, contrasting user or role-based security with code access security.
- Guest Column: Security Framework Defining an enterprise-wide Security Framework. With the emergence of new technology strategies such as Intranets.